Difference between revisions of "Debian with luks"
| (12 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
This tutorial will guide you on installing latest release of Debian 10 (codename Buster) with swap, /home, /root and /var LVM partitions encrypted on top of a LUKS encrypted physical volume. | This tutorial will guide you on installing latest release of Debian 10 (codename Buster) with swap, /home, /root and /var LVM partitions encrypted on top of a LUKS encrypted physical volume. | ||
LUKS, an acronym for Linux Unified Key Setup, offers a standard for Linux hard disk block encryption and stores all the setup data in the partition header. If somehow, the LUKS partition header is tampered, damaged or overwritten in any way, the encrypted data that reside onto this partition is lost. | LUKS, an acronym for [[w:Linux Unified Key Setup|Linux Unified Key Setup]], offers a standard for Linux hard disk block encryption and stores all the setup data in the partition header. If somehow, the LUKS partition header is tampered, damaged or overwritten in any way, the encrypted data that reside onto this partition is lost. | ||
Still, one of the facilities of using LUKS encryption is that you can use a decryption key on the boot process to automatically unlock, decrypt and mount the encrypted partitions, without the need to always type a prompt passphrase at system boot (especially if you are connecting remotely through SSH). | Still, one of the facilities of using LUKS encryption is that you can use a decryption key on the boot process to automatically unlock, decrypt and mount the encrypted partitions, without the need to always type a prompt passphrase at system boot (especially if you are connecting remotely through SSH). | ||
You might ask, why only encrypt the /var and /home partitions and not the entire file system. One argument would be that /home and /var partitions contain, in most cases, sensitive data. While /home partition stores users data, the /var partition stores databases information (typically MySQL database files are located here), log files, websites data files, mail files and other, information that can be easily accessed once a third-party gains physical access to your hard drives. | You might ask, why only encrypt the /var and /home partitions and not the entire file system. One argument would be that /home and /var partitions contain, in most cases, sensitive data. While /home partition stores users data, the /var partition stores databases information (typically MySQL database files are located here), log files, websites data files, mail files and other, information that can be easily accessed once a third-party gains physical access to your hard drives. For security purposes, /root and swap are also encrypted. Swap holds decryption headers somewhere, and the /root, well just safekeep... no more comments here. | ||
== Install == | == Install == | ||
;1. Download Debian | ;1. Download [https://cdimage.debian.org/debian-cd/current/amd64/iso-cd/debian-10.10.0-amd64-netinst.iso Debian 10 ISO] image and burn it to a CD or create a bootable USB drive. Place the CD/USB in your appropriate drive, power on the machine and instruct the BIOS to boot from the CD/USB drive. | ||
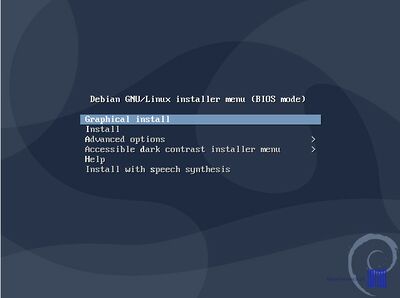
:Once the system boots up the Debian installation media, choose Install from the first screen and press Enter key to move forward. | :Once the system boots up the Debian installation media, choose Install from the first screen and press Enter key to move forward. | ||
| Line 40: | Line 40: | ||
[[File:Debian with luks 14.jpg|400px|center|thumb| Create Disk Partition]] | [[File:Debian with luks 14.jpg|400px|center|thumb| Create Disk Partition]] | ||
;7. Now it’s time to slice the hard drive into partitions. The first partition that will create will be the /( | ;7. Now it’s time to slice the hard drive into partitions. The first partition that will create will be the /boot(boot) partition. Select the FREE SPACE, hit Enter key and choose Create a new partition. Use at least 1 GB as its size and as Primary partition at the Beginning of the disk. | ||
Use as: Ext4 journaling file system | |||
Mount Point: /boot | |||
Label: boot | |||
Bootable flag: on | |||
[[File:Debian with luks 15.jpg|400px|center|thumb| Select Disk Partition]] | [[File:Debian with luks 15.jpg|400px|center|thumb| Select Disk Partition]] | ||
[[File:Debian with luks 16.jpg|400px|center|thumb| Create New Partition]] | [[File:Debian with luks 16.jpg|400px|center|thumb| Create New Partition]] | ||
| Line 52: | Line 58: | ||
Mount Point: / | Mount Point: / | ||
Label: root | Label: root | ||
Bootable flag: | Bootable flag: off | ||
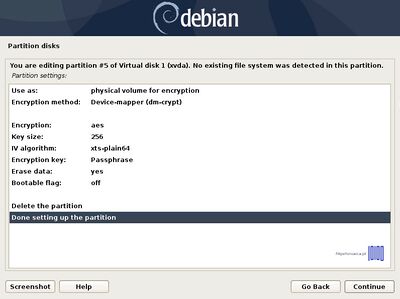
When you have finished setting up the partition choose Done setting up the partition and press Enter to continue further. | When you have finished setting up the partition choose Done setting up the partition and press Enter to continue further. | ||
[[File:Debian with luks 20.jpg|400px|center|thumb| Create Boot Partition]] | [[File:Debian with luks 20.jpg|400px|center|thumb| Create Boot Partition]] | ||
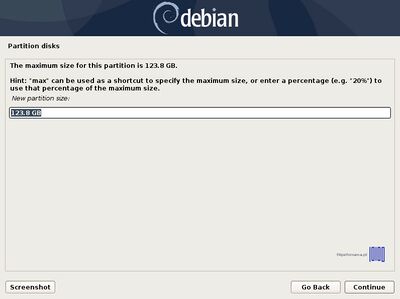
;9. Now it’s time to create the encrypted partition that will be the physical volume for encryption on top of which the LVM /var and /home partition will reside. | ;9. Now it’s time to create the encrypted partition that will be the physical volume for encryption on top of which the LVM swap, /root, /var and /home partition will reside. | ||
To do that, first choose the remaining FREE SPACE -> Create a new partition -> leave the partition size with the default value -> make it a Logical partition -> Use it as Physical volume for encryption -> Done setting up the partition. | To do that, first choose the remaining FREE SPACE -> Create a new partition -> leave the partition size with the default value -> make it a Logical partition -> Use it as Physical volume for encryption -> Done setting up the partition. | ||
| Line 98: | Line 104: | ||
[[File:Debian with luks 40.jpg|400px|center|thumb| Select Device for New Volume]] | [[File:Debian with luks 40.jpg|400px|center|thumb| Select Device for New Volume]] | ||
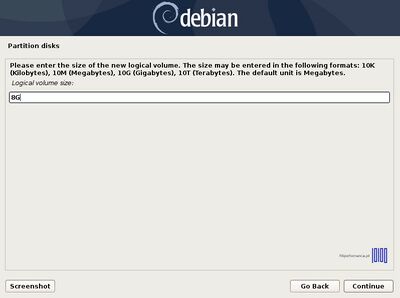
;15. Now, create the Logical Volumes for /home and /var partitions. Choose Create logical volume -> Press Enter at your Volume Group name -> use the home name for the first Logical Volume -> enter a size for home Logical Volume depending on how much space you want to use for your home partition and hit Continue when you’re done. | ;15. Now, create the Logical Volumes for swap, /root, /home and /var partitions. Choose Create logical volume -> Press Enter at your Volume Group name -> use the home name for the first Logical Volume -> enter a size for home Logical Volume depending on how much space you want to use for your home partition and hit Continue when you’re done. | ||
[[File:Debian with luks 41.jpg|400px|center|thumb| Select Logical Volume]] | [[File:Debian with luks 41.jpg|400px|center|thumb| Select Logical Volume]] | ||
[[File:Debian with luks 42.jpg|400px|center|thumb| Set Volume Group Name]] | [[File:Debian with luks 42.jpg|400px|center|thumb| Set Volume Group Name]] | ||
| Line 119: | Line 125: | ||
[[File:Debian with luks 48.jpg|400px|center|thumb| Configure Home Mount Point]] | [[File:Debian with luks 48.jpg|400px|center|thumb| Configure Home Mount Point]] | ||
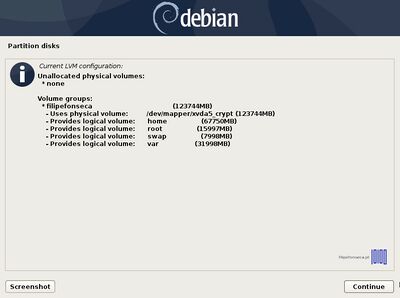
;18. Repeat the above steps for | ;18. Repeat the above steps for remaining Logical Volume with the following settings | ||
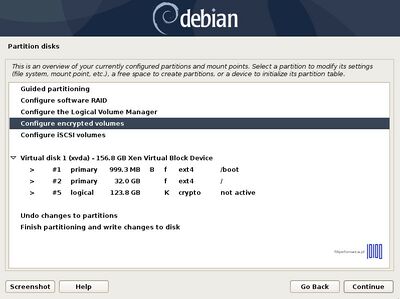
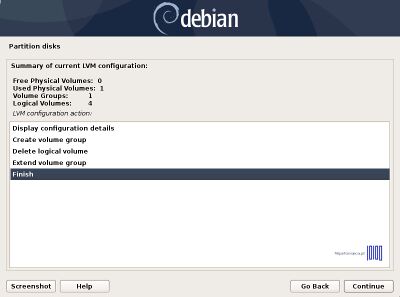
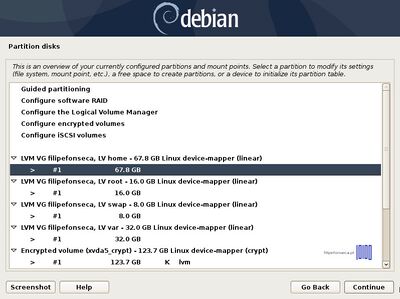
Again, after you finish setting up swap, /root, /home and /var partition hit the Done setting up the partition to return to main Partition menu, review the partitions for a last time, and, if everything is in the right place, move to Finish partitioning and write changes to disk and choose No at the next prompt (Return to partitioning menu) and Yes in order to format the partitions, write changes to disk and continue with the installation process. After base-system is complete, select no to skip another image sources. | |||
Again, after you finish setting up /var partition hit the Done setting up the partition to return to main Partition menu, review the partitions for a last time, and, if everything is in the right place, move to Finish partitioning and write changes to disk and choose No at the next prompt (Return to partitioning menu) and Yes in order to format the partitions, write changes to disk and continue with the installation process. | |||
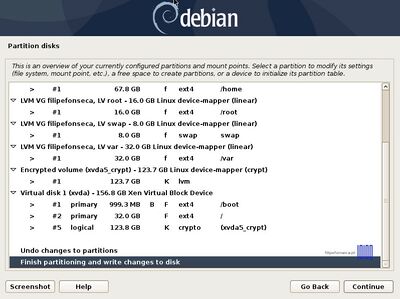
[[File:Debian with luks 50.jpg|400px|center|thumb| Overview of Current Partition]] | [[File:Debian with luks 50.jpg|400px|center|thumb| Overview of Current Partition]] | ||
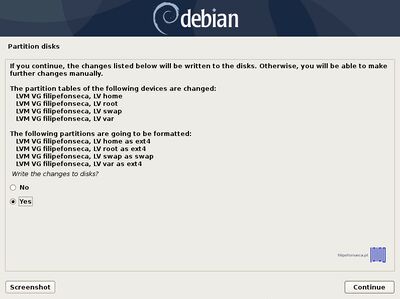
[[File:Debian with luks 51.jpg|400px|center|thumb| | [[File:Debian with luks 51.jpg|400px|center|thumb| Write Changes to Format Disk]] | ||
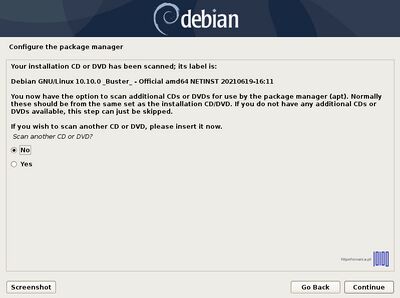
[[File:Debian with luks 52.jpg|400px|center|thumb| | [[File:Debian with luks 52.jpg|400px|center|thumb| Adittional Media]] | ||
;19. That’s all for the partitioning scheme in order to run LVM encrypted partitions on top of an encrypted volume. | ;19. That’s all for the partitioning scheme in order to run LVM encrypted partitions on top of an encrypted volume. | ||
| Line 146: | Line 145: | ||
[[File:Debian with luks 57.jpg|400px|center|thumb| Software Selection]] | [[File:Debian with luks 57.jpg|400px|center|thumb| Software Selection]] | ||
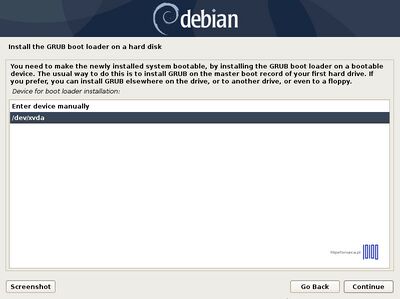
;21. After all the required packages are installed on your system, install the GRUB boot loader to your first hard disk (/dev/ | ;21. After all the required packages are installed on your system, install the GRUB boot loader to your first hard disk (/dev/vxda) MBR (Master Boot Record) and wait for the installation process to finish. | ||
[[File:Debian with luks 58.jpg|400px|center|thumb| Install Grub Loader]] | [[File:Debian with luks 58.jpg|400px|center|thumb| Install Grub Loader]] | ||
[[File:Debian with luks 59.jpg|400px|center|thumb| Select Grub Loader Location]] | [[File:Debian with luks 59.jpg|400px|center|thumb| Select Grub Loader Location]] | ||
| Line 155: | Line 154: | ||
Partitions are now locked with LUKS, only by typing passphrase make the partitions available to boot continuation. | Partitions are now locked with LUKS, only by typing passphrase make the partitions available to boot continuation. | ||
;23. In order to automatically unlock and mount the encrypted | |||
== Auto unlock on boot == | |||
ATTENTION This step will break the purpose of encrypting the system this way. By auto supplying the key on boot, you'll automatically open the partitions, rendering encryption useless. this last annotations are for development testing. | |||
;23. In order to automatically unlock and mount the encrypted partitions during system boot up, login with root user and create a protected key on /root partition by issuing the following commands: | |||
<syntaxhighlight lang="bash"> | <syntaxhighlight lang="bash"> | ||
dd if=/dev/urandom of=cryptkey bs=512 count=1 | # GENERATE KEY | ||
chmod 700 cryptkey | dd if=/dev/urandom of=/cryptkey-sys bs=512 count=1 | ||
# SECURE KEY | |||
chmod 700 /cryptkey-sys | |||
</syntaxhighlight> | </syntaxhighlight> | ||
[[File:Debian with luks | [[File:Debian with luks 62.jpg|400px|center|thumb| Auto Mount Encrypted Partitions]] | ||
This file must be accessible from boot, so it must be placed on unencrypted partition. | |||
;24. After the key has been created, open and edit /etc/crypttab file and replace none parameter with the absolute system path to your key as in the following screenshot: | ;24. After the key has been created, open and edit /etc/crypttab file and replace none parameter with the absolute system path to your key as in the following screenshot: | ||
<syntaxhighlight lang="bash"> | <syntaxhighlight lang="bash"> | ||
# nano /etc/crypttab | # nano /etc/crypttab | ||
</syntaxhighlight> | </syntaxhighlight> | ||
[[File:Debian with luks | [[File:Debian with luks 63.jpg|400px|center|thumb| Add Mount Points]] | ||
;25. Next, add the key to encrypted LUKS device by issuing the following command (LUKS can support up to 8 keys or passphrase slots) and verify if the key has been added to slot number 1: | ;25. Next, add the key to encrypted LUKS device by issuing the following command (LUKS can support up to 8 keys or passphrase slots) and verify if the key has been added to slot number 1: | ||
<syntaxhighlight lang="bash"> | <syntaxhighlight lang="bash"> | ||
cryptsetup luksAddKey /dev/ | # ADD KEY | ||
cryptsetup luksDump /dev/ | cryptsetup luksAddKey /dev/xvda5 /root/cryptkey-sys | ||
#CHECK KEY | |||
cryptsetup luksDump /dev/xvda5 | |||
</syntaxhighlight> | </syntaxhighlight> | ||
[[File:Debian with luks | [[File:Debian with luks 64.jpg|400px|center|thumb| Add Key to Encrypted Luks]] | ||
[[File:Debian with luks | [[File:Debian with luks 65.jpg|400px|center|thumb| Encrypted Key]] | ||
That’s it! On the next boot up process, the encrypted partitions will be automatically unlocked and mounted with the below decryption key | That’s it! On the next boot up process, the encrypted partitions will be automatically unlocked and mounted with the below decryption key. | ||
Be aware that if you lose the decryption key or you forget the passphrase set during installation process the data stored onto the encrypted partitions cannot be recovered and will be forever lost, so you should take precaution and regular backup data, preferably to an encrypted device also. | Be aware that if you lose the decryption key or you forget the passphrase set during installation process the data stored onto the encrypted partitions cannot be recovered and will be forever lost, so you should take precaution and regular backup data, preferably to an encrypted device also. | ||
Latest revision as of 07:02, 14 July 2021
This tutorial will guide you on installing latest release of Debian 10 (codename Buster) with swap, /home, /root and /var LVM partitions encrypted on top of a LUKS encrypted physical volume.
LUKS, an acronym for Linux Unified Key Setup, offers a standard for Linux hard disk block encryption and stores all the setup data in the partition header. If somehow, the LUKS partition header is tampered, damaged or overwritten in any way, the encrypted data that reside onto this partition is lost.
Still, one of the facilities of using LUKS encryption is that you can use a decryption key on the boot process to automatically unlock, decrypt and mount the encrypted partitions, without the need to always type a prompt passphrase at system boot (especially if you are connecting remotely through SSH).
You might ask, why only encrypt the /var and /home partitions and not the entire file system. One argument would be that /home and /var partitions contain, in most cases, sensitive data. While /home partition stores users data, the /var partition stores databases information (typically MySQL database files are located here), log files, websites data files, mail files and other, information that can be easily accessed once a third-party gains physical access to your hard drives. For security purposes, /root and swap are also encrypted. Swap holds decryption headers somewhere, and the /root, well just safekeep... no more comments here.
Install
- 1. Download Debian 10 ISO image and burn it to a CD or create a bootable USB drive. Place the CD/USB in your appropriate drive, power on the machine and instruct the BIOS to boot from the CD/USB drive.
- Once the system boots up the Debian installation media, choose Install from the first screen and press Enter key to move forward.
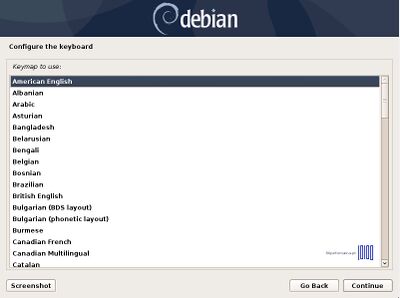
- 2. On the next steps, select the Language for the installation process, select your Country, configure your keyboard and wait for other additional components to load.
- 3. On the next step the installer will automatically configure your Network Card Interface in case you provide network settings through a DHCP Server.
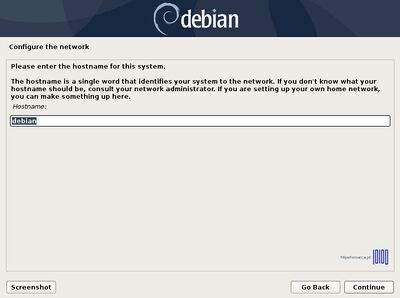
- If your network segment doesn’t use a DHCP server to automatically configure network interface, on the Hostname screen choose Go Back and manually set your interface IP Addresses.
- Once done, type a descriptive Hostname for your machine and a Domain name as illustrated on the below screenshots and Continue with the installation process.
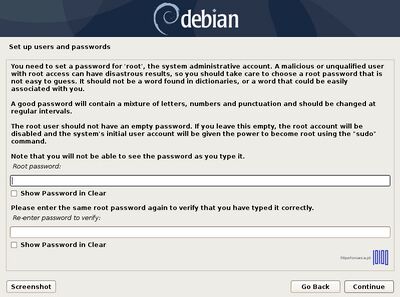
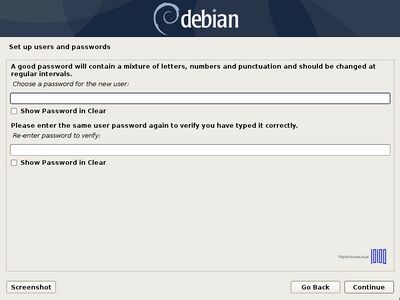
- 4. Next, type a strong password for root user and confirm it, then setup the first user account with a different password.
- 5. Now, setup the clock by selecting your physical nearest time zone.
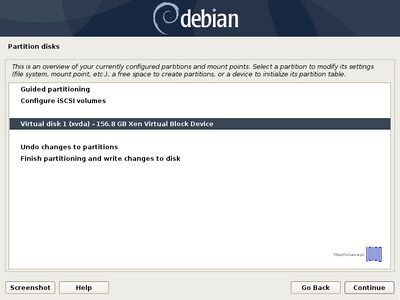
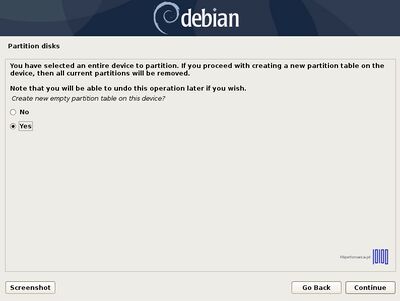
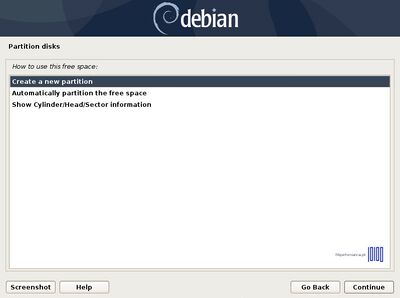
- 6. On the next screen choose Manual Partitioning method, select the hard drive that you want to partition and choose Yes to create a new empty partition table.
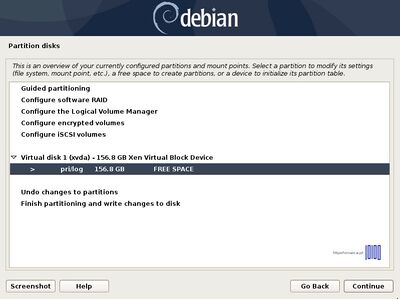
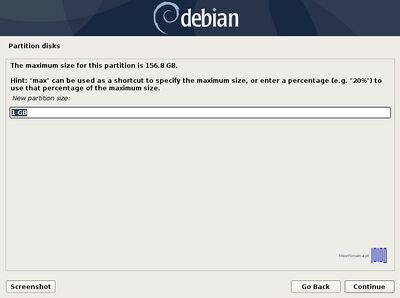
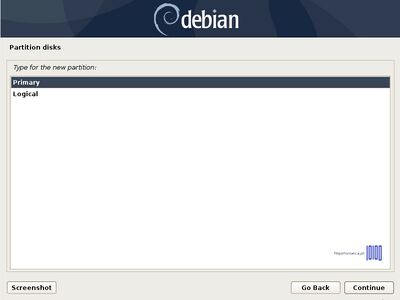
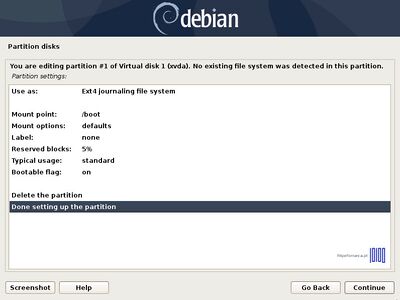
- 7. Now it’s time to slice the hard drive into partitions. The first partition that will create will be the /boot(boot) partition. Select the FREE SPACE, hit Enter key and choose Create a new partition. Use at least 1 GB as its size and as Primary partition at the Beginning of the disk.
Use as: Ext4 journaling file system
Mount Point: /boot
Label: boot
Bootable flag: on
- 8. Next, configure /(root) partition with the following settings
Use as: Ext4 journaling file system Mount Point: / Label: root Bootable flag: off
When you have finished setting up the partition choose Done setting up the partition and press Enter to continue further.
- 9. Now it’s time to create the encrypted partition that will be the physical volume for encryption on top of which the LVM swap, /root, /var and /home partition will reside.
To do that, first choose the remaining FREE SPACE -> Create a new partition -> leave the partition size with the default value -> make it a Logical partition -> Use it as Physical volume for encryption -> Done setting up the partition.
Use the below screenshots as a guidance for this steps.
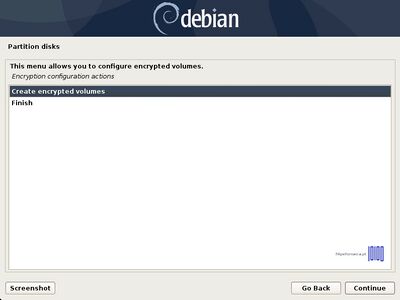
- 10. After the Physical volume for encryption has been created it’s time to configure the Encrypted volumes. If you have other partitions or hard drives that you want to use for encryption, now it’s time to create them all by repeating the above steps for each partition on hard drives.
To move forward, next select Configure encrypted volumes and hit on Yes to write the changes to disk and start configure encrypted volumes.
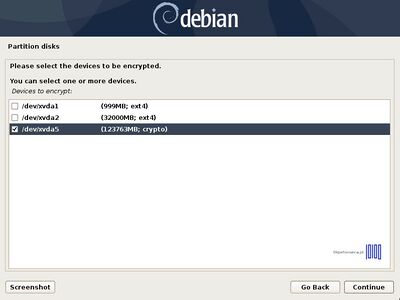
- 11. On the next screen choose Create encrypted volumes and choose the devices (partitions) to encrypt. If you have a hard time to recognize the correct devices that will be used for encryption after their partition number or size, just look after a crypto word at the end of each listed partition.
To select the partitions use up and down keys to navigate and press the space key to select the appropriate partitions and an asterisk should appear on the selected device. When you’re done with devices selection, hit the Tab key to jump on Continue and press Enter key to move forward and Finish.
- 12. On the next screen the installer will ask you whether you want to erase the data on the encrypted partitions. Depending on your available time or if the hard disk it’s new and has just been partitioned, so it does not contain any data, choose No and provide a strong passphrase for the encrypted volume.
When you’re done with the passphrases hit Continue to return to main Partition menu and configure LVM volumes further.
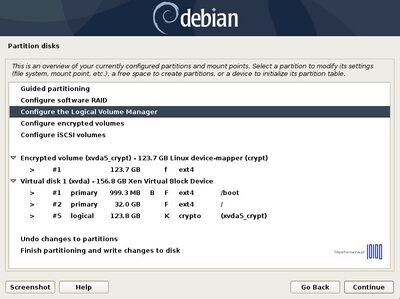
- 13. Once you have returned at the main Partition menu, it’s time to create the LVM partitions for swap, /root /home and /var on top of the encrypted volume.
Next, select Configure the Logical Volume Manager and confirm (Yes) the new write changes to disk.
- 14. On the next step create a Volume Group using a descriptive name for this VG (for this setup we used the name filipefonseca) and select the encrypted device (partition) that will be a part of the VG by pressing the space key. To jump to Continue menu press the Tab key.
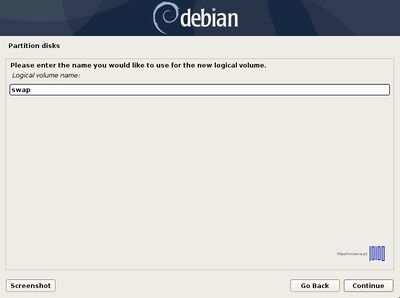
- 15. Now, create the Logical Volumes for swap, /root, /home and /var partitions. Choose Create logical volume -> Press Enter at your Volume Group name -> use the home name for the first Logical Volume -> enter a size for home Logical Volume depending on how much space you want to use for your home partition and hit Continue when you’re done.
- 16. Next, repeat the above step in order to create the remaining Logical Volume and hit Finish when you’re done to go back to main Partition menu.
- 17. Once returned to the main Partition menu it’s time to configure the LVM partitions settings and mount points. Navigate to #1 home Logical Volume and configure the LVM partition with the following settings
Use as: Ext4 journaling file system
Mount Point: /home
Label: home
When you finish hit the Done setting up the partition.
- 18. Repeat the above steps for remaining Logical Volume with the following settings
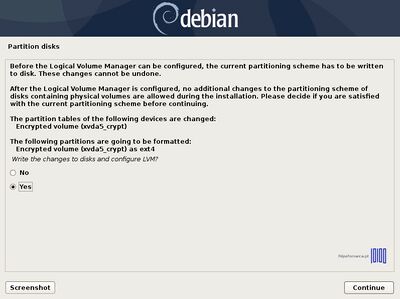
Again, after you finish setting up swap, /root, /home and /var partition hit the Done setting up the partition to return to main Partition menu, review the partitions for a last time, and, if everything is in the right place, move to Finish partitioning and write changes to disk and choose No at the next prompt (Return to partitioning menu) and Yes in order to format the partitions, write changes to disk and continue with the installation process. After base-system is complete, select no to skip another image sources.
- 19. That’s all for the partitioning scheme in order to run LVM encrypted partitions on top of an encrypted volume.
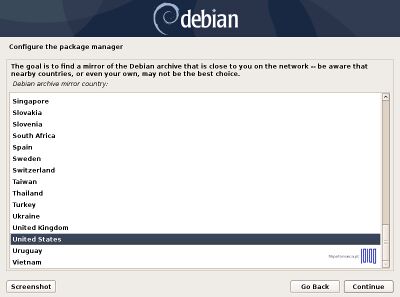
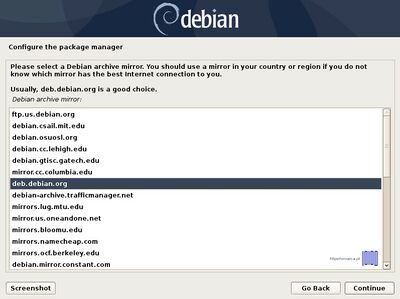
After the base system is installed, select a Debian archive mirror country for repositories. If the machine is directly connected to Internet and you do not use a proxy server to gain Internet access, hit on Continue at HTTP proxy information.
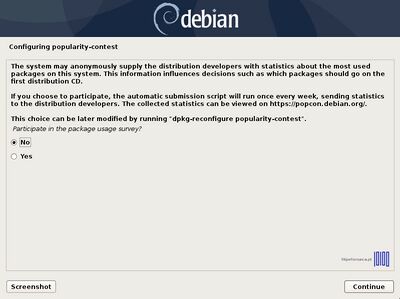
- 20. After the installer will configure the apt repositories a new prompt should appear demanding to participate in the package usage survey. Choose No to continue and select the software you want to install further.
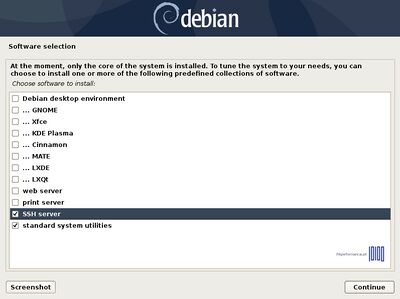
Depending on the final destination of your machine, you can opt for a Graphical User Interface with your favorite Desktop environment (Gnome, Xfce, KDE, Cinnamon, MATE, LXDE) or a server configuration with no GUI.
In any case, choose standard system utilities and SSH if you want to use the machine as a server and hit Continue when you’re done.
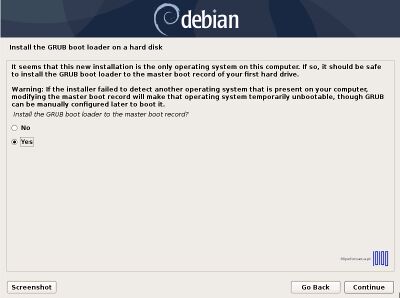
- 21. After all the required packages are installed on your system, install the GRUB boot loader to your first hard disk (/dev/vxda) MBR (Master Boot Record) and wait for the installation process to finish.
- 22. After the installation finishes hit Continue to reboot the machine. At the booting process you will be asked to enter the passphrase configured on the installation process in order to unlock the encrypted device and mount the encrypted partitions.
Partitions are now locked with LUKS, only by typing passphrase make the partitions available to boot continuation.
Auto unlock on boot
ATTENTION This step will break the purpose of encrypting the system this way. By auto supplying the key on boot, you'll automatically open the partitions, rendering encryption useless. this last annotations are for development testing.
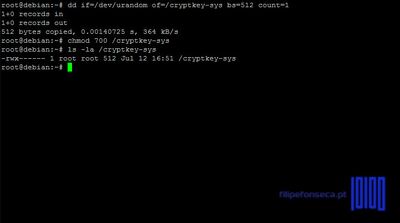
- 23. In order to automatically unlock and mount the encrypted partitions during system boot up, login with root user and create a protected key on /root partition by issuing the following commands
# GENERATE KEY
dd if=/dev/urandom of=/cryptkey-sys bs=512 count=1
# SECURE KEY
chmod 700 /cryptkey-sysThis file must be accessible from boot, so it must be placed on unencrypted partition.
- 24. After the key has been created, open and edit /etc/crypttab file and replace none parameter with the absolute system path to your key as in the following screenshot
# nano /etc/crypttab- 25. Next, add the key to encrypted LUKS device by issuing the following command (LUKS can support up to 8 keys or passphrase slots) and verify if the key has been added to slot number 1
# ADD KEY
cryptsetup luksAddKey /dev/xvda5 /root/cryptkey-sys
#CHECK KEY
cryptsetup luksDump /dev/xvda5That’s it! On the next boot up process, the encrypted partitions will be automatically unlocked and mounted with the below decryption key.
Be aware that if you lose the decryption key or you forget the passphrase set during installation process the data stored onto the encrypted partitions cannot be recovered and will be forever lost, so you should take precaution and regular backup data, preferably to an encrypted device also.